Can’t Play the Video Given to You in Discovery?
August 5, 2022
Hospitals are Violating Federal Law by Blocking the Release of a Child’s Full Medical Records
November 9, 2022
Can’t Play the Video Given to You in Discovery?
August 5, 2022
Hospitals are Violating Federal Law by Blocking the Release of a Child’s Full Medical Records
November 9, 2022Cell Phone Forensic Images Are Not All the Same
Did you know there are multiple types of forensic images ranging from a little amount of data to all data?
Do you know the difference?
Forensic imaging tools allow the operator to select as easy as choosing flavors of ice cream, different types of forensic images. Each type of forensic image contains drastically different amounts of data.
Even if selecting the type of forensic image that contains the most amount of data, the expert may select only partial data to create a Cellebrite Reader Report leaving you wondering if you have all the data.
Would you know if you were missing data?
Let’s take a minute to explore what options are available when creating a forensic image (extraction) of a cell phone.
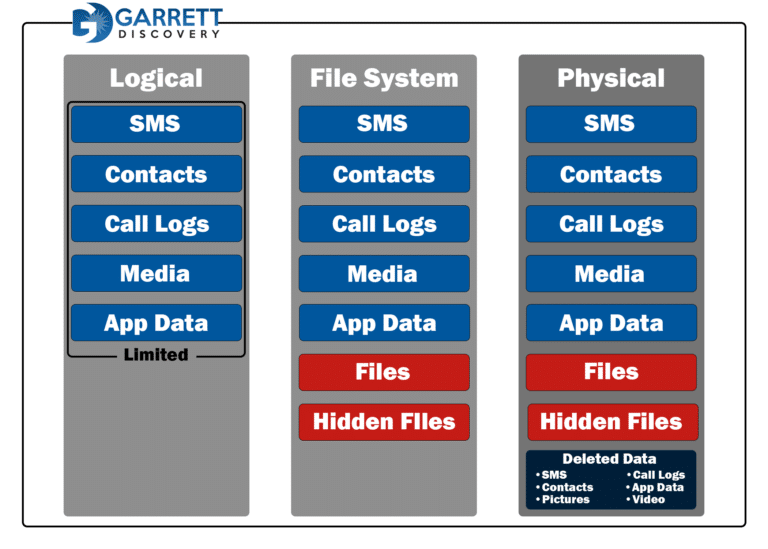
Below is a chart that shows the differences between each extraction type.
Now wait a minute… Are we saying that you need to perform a Physical Extraction of the phone to get the deleted data?
Yes, but that is not available for all phones and if you are looking outside of law enforcement at the time of this writing, there are only three firms in the US that possess this ability for iPhone and Android phones and we are one of those firms. The tools to perform a Physical Extraction re extremely expensive and, in most cases, if you are not dealing with a very large forensic firm, they just would not be able to afford such a tool? The tools to do this restricted to government and a few select firms and even those firms deal with NDA’s as to their capabilities.
Law Enforcement predominantly uses Cellebrite tools for mobile phones. This software comes in different versions. The least expensive which still costs as much as a car is UFED4PC and can create Logical Images and some File System Images of certain makes and models of phone. The next version is Premium which can create Physical Images, but is typically cost prohibitive unless it is purchased at a center with a sophisticated forensic lab and can be 20-30x the cost yearly to run over UFED4PC. Typically we see this being used at larger labs or Regional Computer Forensic labs serving a large area of a state.
What if the device is locked?
There are forensic tools for unlocking phones that is restricted to law enforcement and a handful of civilian labs with us being one of those labs. This is the subject of a different article, published soon. This depends on what you are seeking. If you are looking for more data that can be found in a file system extraction than maybe that is something law enforcement can create. If you seek deleted data, you may have to ask for the device to be shipped to another law enforcement center with the capabilities to create a Physical Image of the phone. This happens all the time in cases we are involved in and in most cases law enforcement will give you what you are asking for to avoid an order allowing a defense examiner to touch the original evidence. What I can say is that by having a competent forensic expert in your corner to advise you as to whether or not you need to ask for a forensic image that contains more data is very important. Additionally, the expert should discuss with you the risk of analyzing more data where law enforcement may find evidence of other crimes or additional information to be used at trial.
Is Exculpatory information important?
Yes, we often are able to build alibi defense, evidence that puts conversations into context and evidence that puts witnesses into bad light. This is very important considering the only data that will be presented at trial is data that is helpful to the prosecution.
For instance, in our Title IX cases we often find deleted text messages where an alleged female victim was bragging to a friend about sleeping with another college student prior to saying that she was assaulted by the student. We have found many cases where the alleged victim made up the assault in an attempt to get back at someone for sleeping around.
We have worked on over 3,400 cases, some of those cases were dismissed over data found on a mobile phone that exonerated our clients. Call us to discuss. We don’ t work in the world of unicorns or fairy tales or the big win that cannot be replicated. We work in the world of repeatable methods that can bring value to your case.
NEVER PLAY CARDS WITH HALF A DECK!
If you need assistance in navigating the world of cell phone forensics or any other type of digital forensics, we have a staff of 41 that are here to assist you.
