Digital Audio Forensic Analysis of Files
January 24, 2023
Forensics v. eDiscovery Preservation Methods
January 24, 2023WHAT IS PEGASUS?
Pegasus is spyware made by NSO Group. NSO Group, which also goes by the name Q-Cyber, is an Israeli cyber warfare technology firm. Novalpina Capital, a European private equity firm, owns a majority stake in NSO Group.
Pegasus is a spyware suite, with multiple delivery vectors. The WhatsApp exploit from May 2019 is one such vector. Others include tricking targets into clicking on a link using social engineering. Not all vectors are publicly known. Once the spyware is implanted it provides the operators with regular, scheduled updates and is designed to avoid excessive bandwidth consumption.
Development of capabilities
The earliest version of Pegasus – which was identified in 2016 – relied on a spear-phishing attack which required the target to click a malicious link in a text message or email.
As of August 2016 – according to a former NSO Employee – the U.S. version of Pegasus had 1-click capabilities for all phones apart from old Blackberry models which could be infiltrated with a 0-click attack.
In 2019, WhatsApp revealed Pegasus had employed a vulnerability in its app to launch zero-click attacks (the spyware would be installed onto a target’s phone by calling the target phone; the spyware would be installed even if the call was not answered).
Since 2019, Pegasus has come to rely on iPhone iMessage vulnerabilities to deploy spyware.
By 2020, Pegasus shifted towards zero-click exploits and network-based attacks. These methods allowed clients to break into target phones without requiring user interaction and without leaving any detectable traces.
CALL TO ACTION: CALL GARRETT DISCOVERY EXPERTS AT 888.822.5077
Data Collection
According to the purported NSO Group documentation, once successfully implanted on a phone using an exploit chain like the Trident, Pegasus can actively record or passively gather a variety of different data about the device.
Pegasus Can Listen In On Your Phone Calls and Read Your Messages
By giving full access to the phone’s files, messages, microphone and video camera, the operator is able to turn the device into a silent digital spy in the target’s pocket.
Persistence
Research shows Pegasus can perform chip level attacks (this means it can run within IC (integrated chip) the core processor of the device, it is however only found that Pegasus chip level attacks are confirmed in some Android devices but not on iOS, a full DFU Operating system restore on an iDevice would be the only proposed way to get rid of the spyware.
Forensics Method to find Pegasus related artifacts
- Discovering Pegasus network injection attacks
- Pegasus’ bridge head and other malicious processes
- Pegasus processes following potential Apple Photos exploitation
- iMessage
- Apple Music
- System Databases
- System Services
- NSO attack Domains
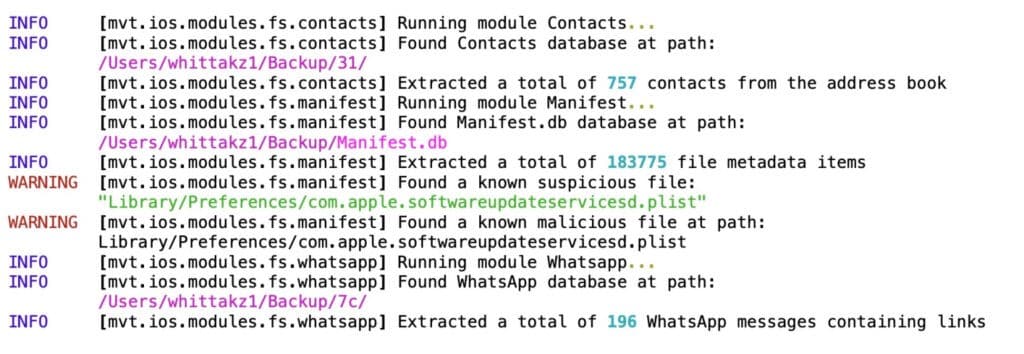
Forensic Detection using MVT Framework
To trace one of the world’s most sophisticated spyware programs, MVT relies on running forensic scans that look for “Indicators Of Compromise” or IOCs. These IOCs are basically signs that are believed to exist on every Pegasus-infected device.
An example of an IOC could be a domain address used by Pegasus’s creator, the NSO Group, in its operations. In infected phones, this domain name might reside inside an SMS or an e-mail.
Snapshot of an MVT scan