
Deciphering NCMEC Cybertips
June 16, 2025


Garrett Discovery was called upon by multiple news outlets to examine the purported RAW surveillance video from the Metropolitan Correctional Center (MCC) in New York, where Jeffrey Epstein, accused of sex trafficking, was detained. This analysis, initially was conducted for Inside Edition within a four-hour timeframe.
Jeffrey Epstein was held at MCC for 35 days from July 6, 2019, until his death on August 10, 2019, under suspicious circumstances. The Department of Justice (DOJ) reported that two cameras outside Epstein’s cell malfunctioned, and a third camera’s footage was unusable, with the footage sent to the FBI’s crime lab in Quantico, Virginia, for analysis. The DOJ Office of Inspector General (OIG), led by Michael Horowitz, in a public statement concluded that technical errors, not sabotage, caused the lack of recorded footage. However, public skepticism persists due to the high-profile nature of the case. The DOJ released what it claims is the raw footage, accessible at: https://www.justice.gov/video-files/video1.mp4.
Forensic Analysis Findings
File metadata, distinct from operating system metadata (e.g., modified, accessed, or created dates), is embedded within the file and persists during transfers, such as uploads to a web server. Our analysis revealed:
The video file originated from a temporary directory within the user profile “MJCOLE~1” on a Windows computer, as indicated by the file path. This contrasts with file paths typical of Apple systems.
The metadata indicates the video file was derived from a .PRProj file, an Adobe Premiere Project file. Adobe Premiere is a professional video editing and mastering software, not used in surveillance systems, raising concerns about the file’s authenticity as “raw” footage.
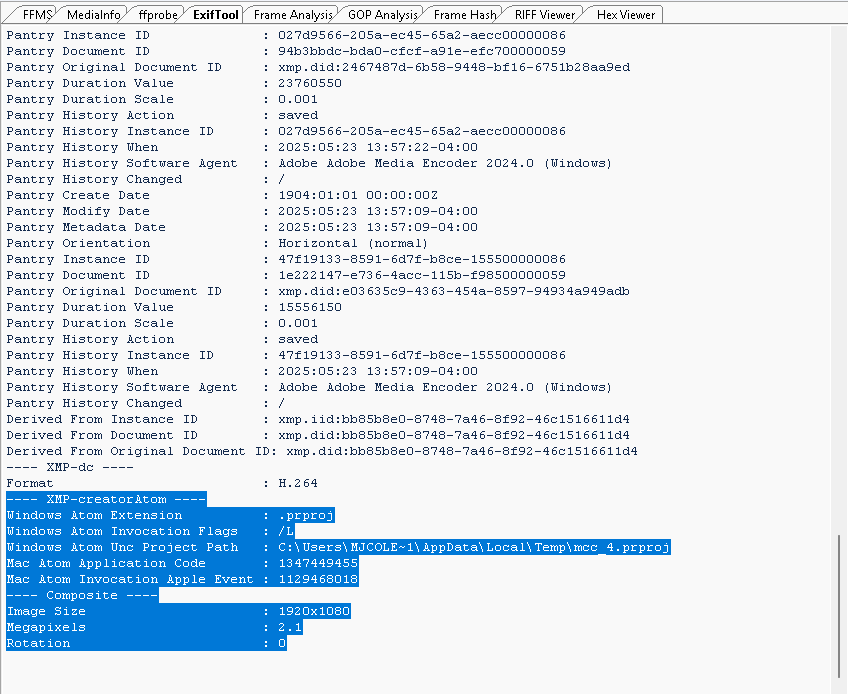
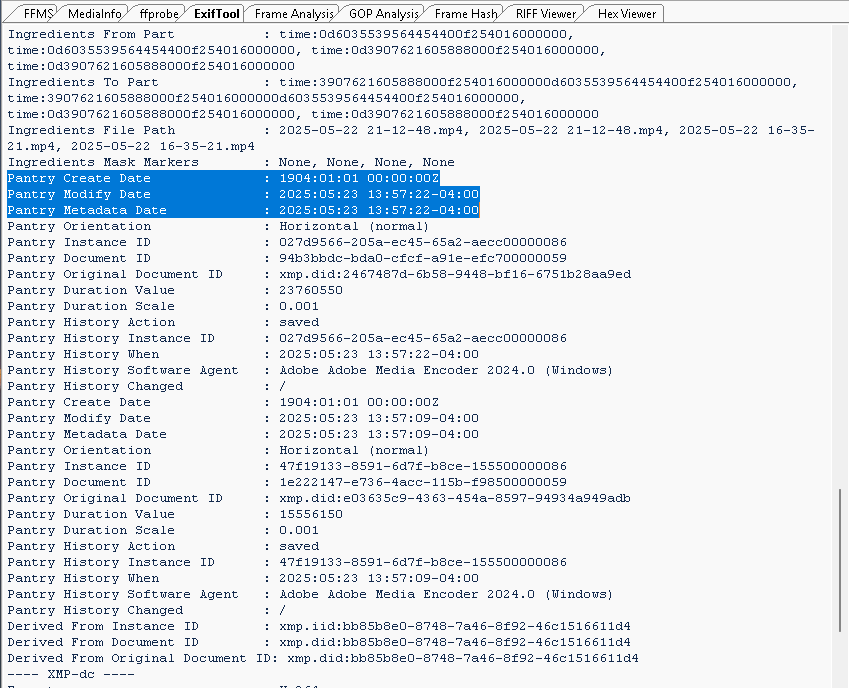
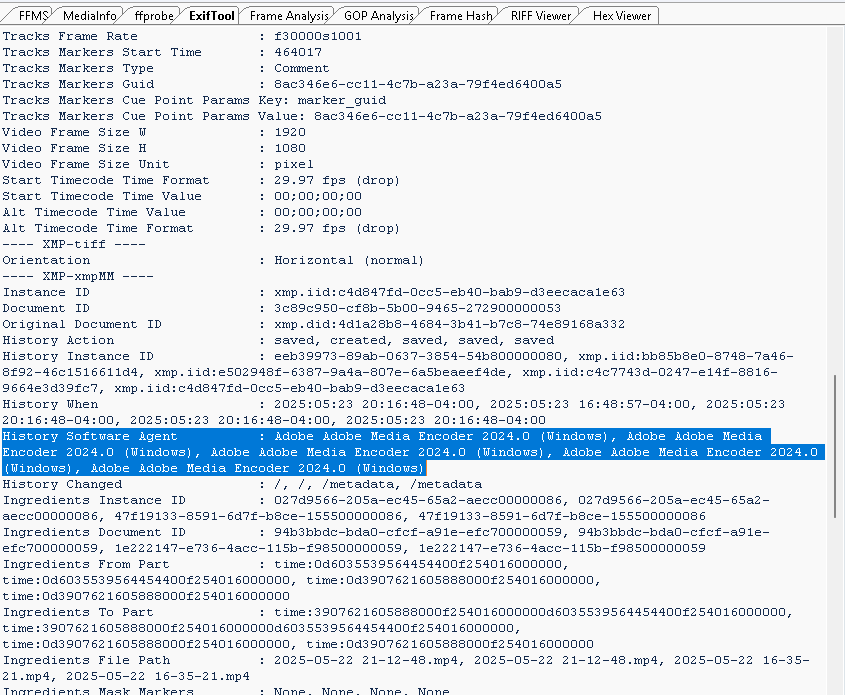
The metadata shows the video file, video1.mp4, was created from the Adobe Premiere project on May 23, 2025, at 16:48:57 UTC-4 (4:48 PM EDT, accounting for Eastern Daylight Time). A subsequent save occurred 3 hours and 38 minutes later, on May 23, 2025, at 20:16 EDT, suggesting either a modification or an unnecessary save. Each save recorded Adobe as the encoder, further indicating post-production editing.
A visual inspection of the video revealed:



Having directly inspected 25 jail DVR systems, including in Carlock v. Williamson—where unfettered access exposed repositioned cameras, deleted files, and spoliation leading to attorneys’ temporary license suspensions for assisting the jail in spoliation of evidence.
I think the DOJ has a lot of explaining and the public should not be satisfied until they do.