Garrett Discovery Named Affinity Partner by National Association of Criminal Defense Lawyers
February 5, 2025




NCMEC Cybertips are frequently misread or misunderstood due to the complex language used in them. This misunderstanding is shared by law enforcement, prosecutors, and defense attorneys alike. In this article, I aim to clarify some key aspects of NCMEC Cybertips.
Under 18 U.S.C. 2258A, electronic service providers (ESPs) such as Snapchat, Instagram, Facebook, and X are required to report “apparent child pornography” to the National Center for Missing and Exploited Children (NCMEC).
NCMEC is a non-profit organization established by Congress. One of its key functions is managing the CyberTipline, which serves as a clearinghouse for complaints of child sexual exploitation and child pornography. NCMEC reviews incoming reports and refers them to the appropriate law enforcement agency, typically a regional Internet Crimes Against Children (ICAC) task force.
While not all providers have direct access to NCMEC’s system or permission to submit tips electronically, the CyberTipline Reporting system serves as the central point for ESPs to report incidents. Companies can submit details such as the time and date of the reporting incident, email address, screen name, IP address, and all suspected images and videos.
NCMEC requests that ESPs retain a copy of the reported files for 90 days.
There are several methods:
Please pay special attention to the following details.

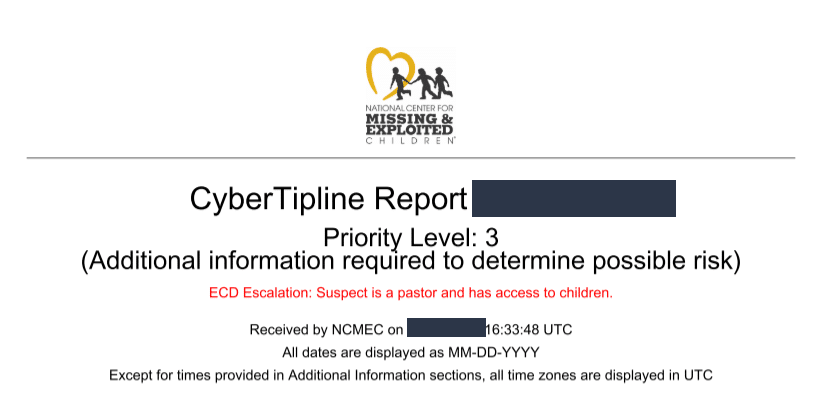
This section contains a brief description of the incident, the time of the incident, the webpage involved, and the email, username, and IP address of the reported individual. The IP address provided is directly related to the report, such as the address used to upload the offending files. It’s crucial to note that the incident time refers to when the file was detected on the ESP’s network, not the date and time of the alleged crime.
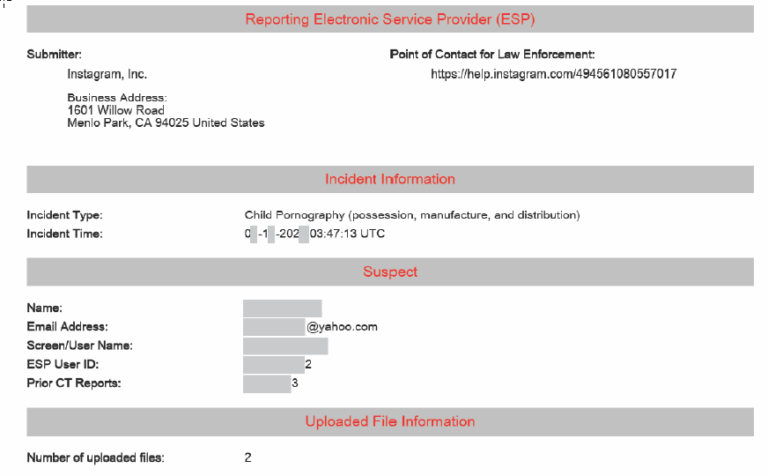
For example, if a suspect has a file of child pornography in their Dropbox from February 2022 to the present, and NCMEC distributes a new hash list in January 2025 that includes the hash of that file, the incident date would be in January 2025. This date does not reflect the actual time of the alleged crime.
At the end of Section A, information about each uploaded file is provided. For each file, it should indicate whether the reporting ESP viewed the file and whether it was publicly available. If the ESP did not provide this information, it will state “(Information Not Provided by Company)”. This is significant because if the file was not publicly available, a distribution charge may not be appropriate.
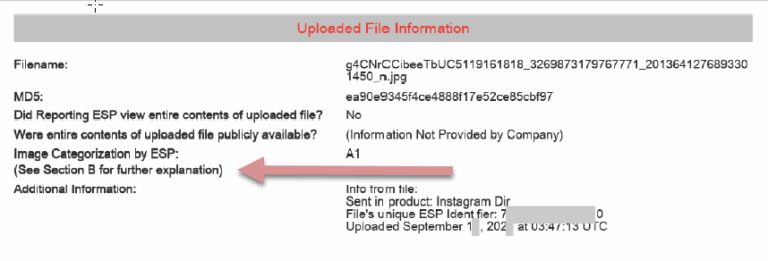
Pay particular attention to the “Image Categorization by ESP”. Although it appears in Section A as if it came from the ESP, the files are not actually categorized by the ESP. The statement “See Section B for further explanation” indicates that NCMEC adds this categorization. This is done to assist law enforcement, who can then state in search warrants that the ESP categorized the file as child pornography, even though the process is entirely automated.
This section includes geolocation information for the IP address associated with the report. The location provided is approximate and should only be used to identify the appropriate law enforcement agency or task force, not for securing a warrant or identifying a suspect. The latitude and longitude are typically based on the state or city linked to the IP address and often represent a central point in the city rather than a specific address. The Internet Service Provider (ISP) that owns or controls the IP address is also listed. If the IP address is associated with a residential ISP, investigators can use a subpoena to obtain subscriber information and the service address for the account at the time of the offense.
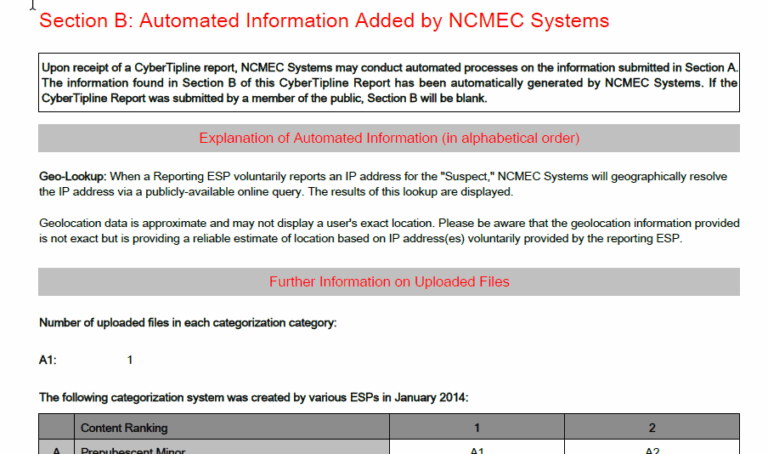
This section contains any additional information, which may include references to other CyberTipline Reports linked to the same username or IP address. It may also include unverified information from public websites.
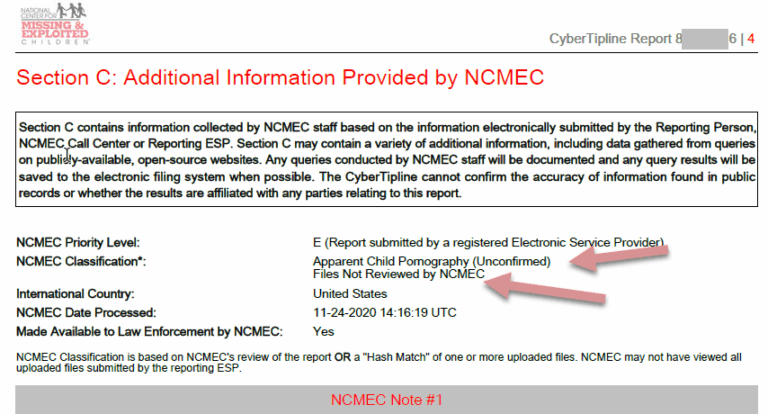
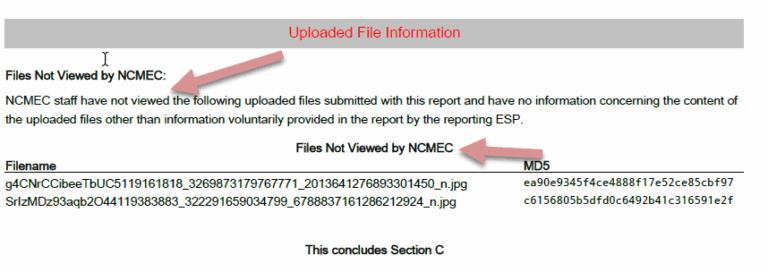
A point of confusion is that the ESP may state they did not review the file’s contents but still provide a categorization. Meanwhile, NCMEC claims they did not review the contents but attributes the categorization to the ESP. In reality, ESPs receive hash lists without categorizations, and it is NCMEC that adds this information. The language in Cybertips is designed to suggest that the ESP or NCMEC reviewed the file, but the process is automated. Law enforcement often requests search warrants without accessing the ICAC Data Systems VPN to view the files. If you need assistance in proving that the files were not accessed prior to applying for a search warrant call us.
This section provides the contact information for the law enforcement agency to which NCMEC submitted the report.
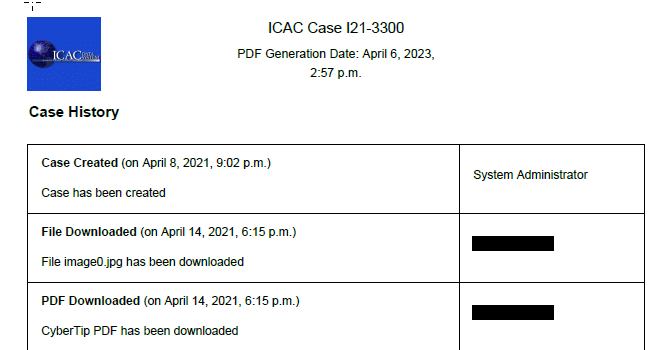
The Department of Justice’s Office of Juvenile Justice and Delinquency Prevention (DOJ OJJDP) developed a system to route Cybertips and associated contraband files to the appropriate local law enforcement entity based on the IP address of the alleged offender. This system is known as the ICAC Data Systems or Deconfliction. Through this system, it is possible to determine when an officer downloaded the Cybertip and the contraband files, as well as whether the investigation was initiated within or outside their jurisdiction. Below is a sample showing the download of a Cybertip.